Gradle partners with GitHub on supply chain security
Table of Contents
Introduction
Gradle is happy to announce a technical partnership with GitHub focusing on multiple areas, starting with supply chain security and developer experience. With this partnership, we establish a direct connection between organizations and plan to cooperate on integrations between GitHub and Gradle to promote best security practices among Gradle users.
The first feature being released as a part of this partnership is the dependency submission GitHub Action for Gradle, which can be configured to automatically submit dependencies to GitHub’s dependency graph, helping users better understand their application and receive Dependabot alerts.
This partnership will improve the experience of many users within the shared Gradle and GitHub ecosystem. GitHub is the world’s leading AI-powered developer platform to build, scale, and deliver secure software, home to more than 284 million public repositories. Gradle Build Tool is the default build system for Android application development, the most used JVM build system on GitHub, and among the most used build systems on the GitHub platform across public and private repositories.
“Gradle is one of the most used build tools among GitHub users, and we’re excited to continue to collaborate with them to improve supply chain security for the Gradle community. These updates to the Gradle Build Action will help millions of GitHub users improve the security of their apps by giving them better insights into their dependencies.” - Jon Janego, Senior Product Manager at GitHub
The problem with vulnerable dependencies #
Vulnerable project dependencies are a major risk for the software ecosystem. It’s critical for developers to quickly detect potential vulnerabilities arising from both direct and transitive dependencies. It is a priority for many modern build systems, including Gradle, to help developers manage their dependencies and protect the supply chain and end users.
Gradle Build Tool provides advanced security features like dependency verification and other tools to protect project integrity. GitHub offers many security features to deal with this problem, including Dependabot alerts, that detects if a repository uses a dependency with known vulnerabilities, and notifies maintainers. However, until recently, first-class integration between Dependabot alerts and Gradle Build Tool was missing.
Dependency management is a hard problem. Some naive approaches to dependency reporting attempt to parse build files to determine dependency versions; however, this only works for the simplest cases, as dependency versions can be influenced by many factors. For example, conflict resolution can result in a different version being used than the ones declared in the build sources. In the case of Gradle, plugins and various dependency management features can also affect the dependency version. Additionally, dependencies can also be declared in different buckets and across many subprojects. Today’s announcement introduces a new way to address this challenge.
Announcing new Dependency Submission Action #
The Dependency Submission Action for Gradle is now ready for broad adoption by those using GitHub or GitHub Enterprise instances. You can find this on the GitHub Actions Marketplace.
The Dependency Submission Action for Gradle is an official and open-source GitHub action that generates complete and accurate information about dependencies in Gradle projects and uploads this to GitHub. This information allows maintainers to view the dependencies of their projects in GitHub and get notified when vulnerable dependencies are detected.
Once the action is enabled, the dependencies are visible in the dependency graph view of the project.
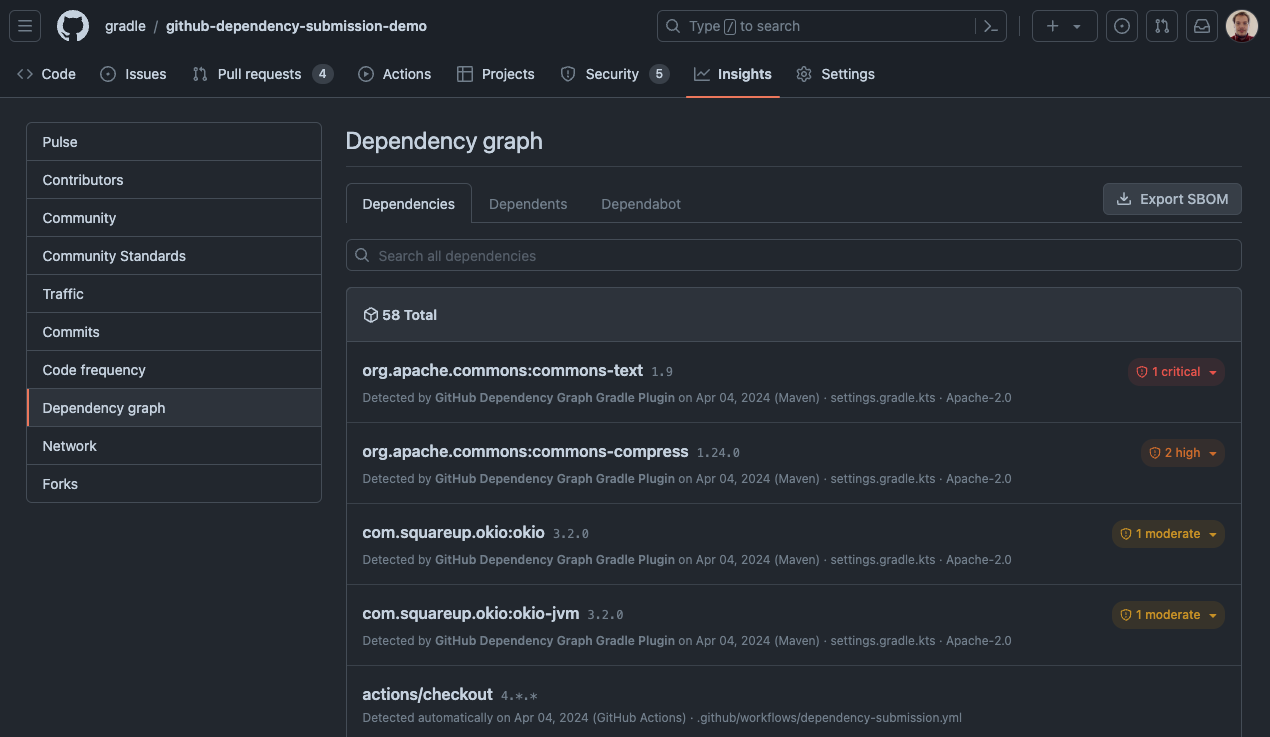
When a vulnerable dependency is detected, project admins and maintainers can be automatically notified via Dependabot alerts. The vulnerable dependencies are also displayed in the Security > Vulnerability alerts > Dependabot view of the project:
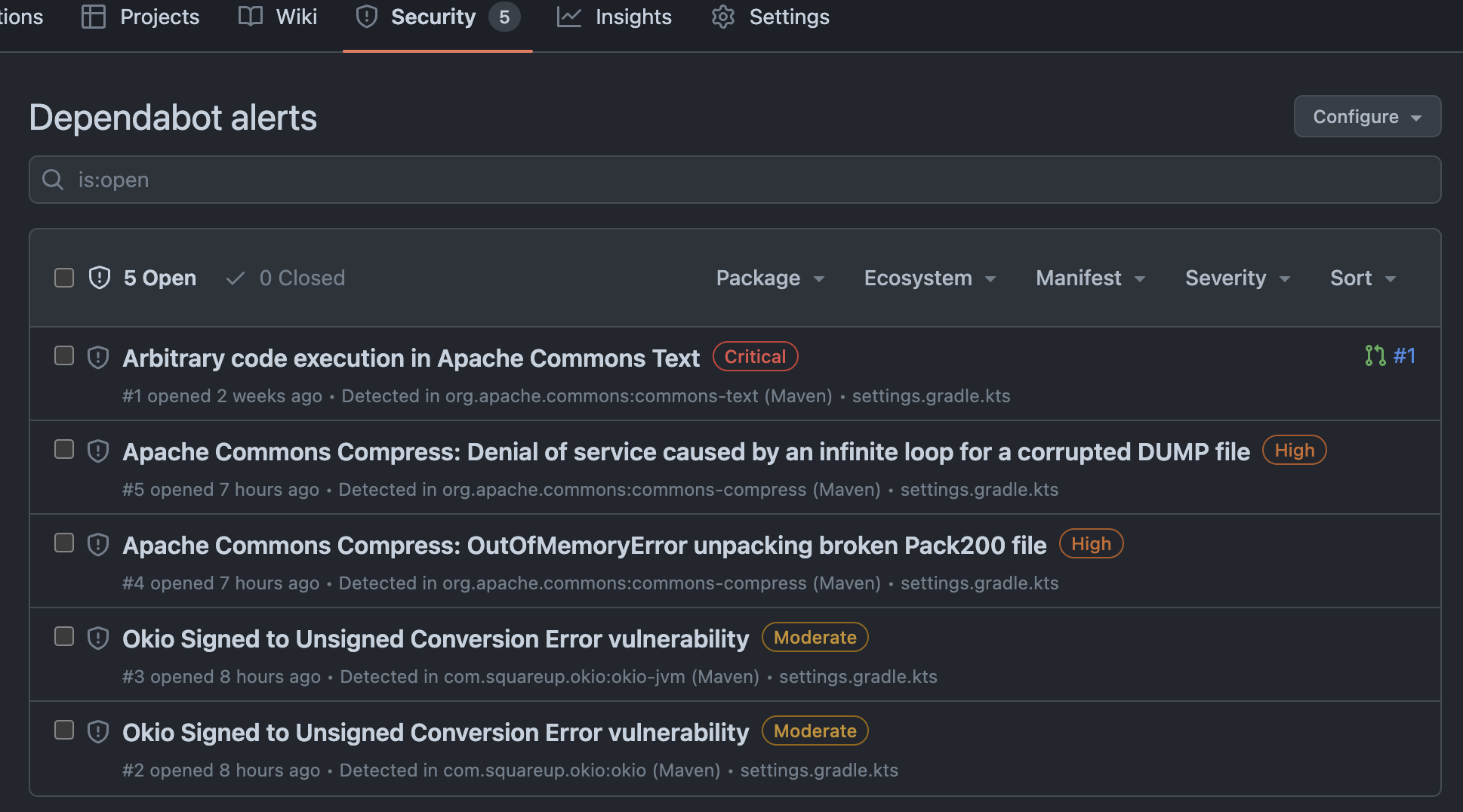
Dependency Submission Action for Gradle provides a reliable way to inspect dependencies in Gradle projects and get alerts about discovered vulnerabilities. We highly recommend enabling it in your projects. Since this only requires a small GitHub Actions configuration, let’s see how to do this…
How to use the Dependency Submission Action #
The Dependency Submission Action is ready for wide adoption and we recommend that all Gradle projects on GitHub use it. To use Dependency Submission Action, follow the steps in the readme.
For basic usage, you need a simple YAML file in .github/workflows/ directory of your repository, for example, .github/workflows/dependency-submission.yml:
name: Dependency Submission
on:
push:
branches: [ "main" ]
permissions:
contents: write
jobs:
dependency-submission:
runs-on: ubuntu-latest
steps:
- name: Checkout sources
uses: actions/checkout@v4
- uses: actions/setup-java@v4
with:
distribution: 'temurin'
# change if your project requires a different Java version
java-version: '17'
- name: Generate and submit dependency graph
uses: gradle/actions/dependency-submission@v3
You can see a live example of this GitHub Workflow here. The source file of the GitHub definition can be found in .github/workflows/dependency-submission.yml. Once the first push is executed or you trigger the dependency submission manually, you will be able to see the following build output:
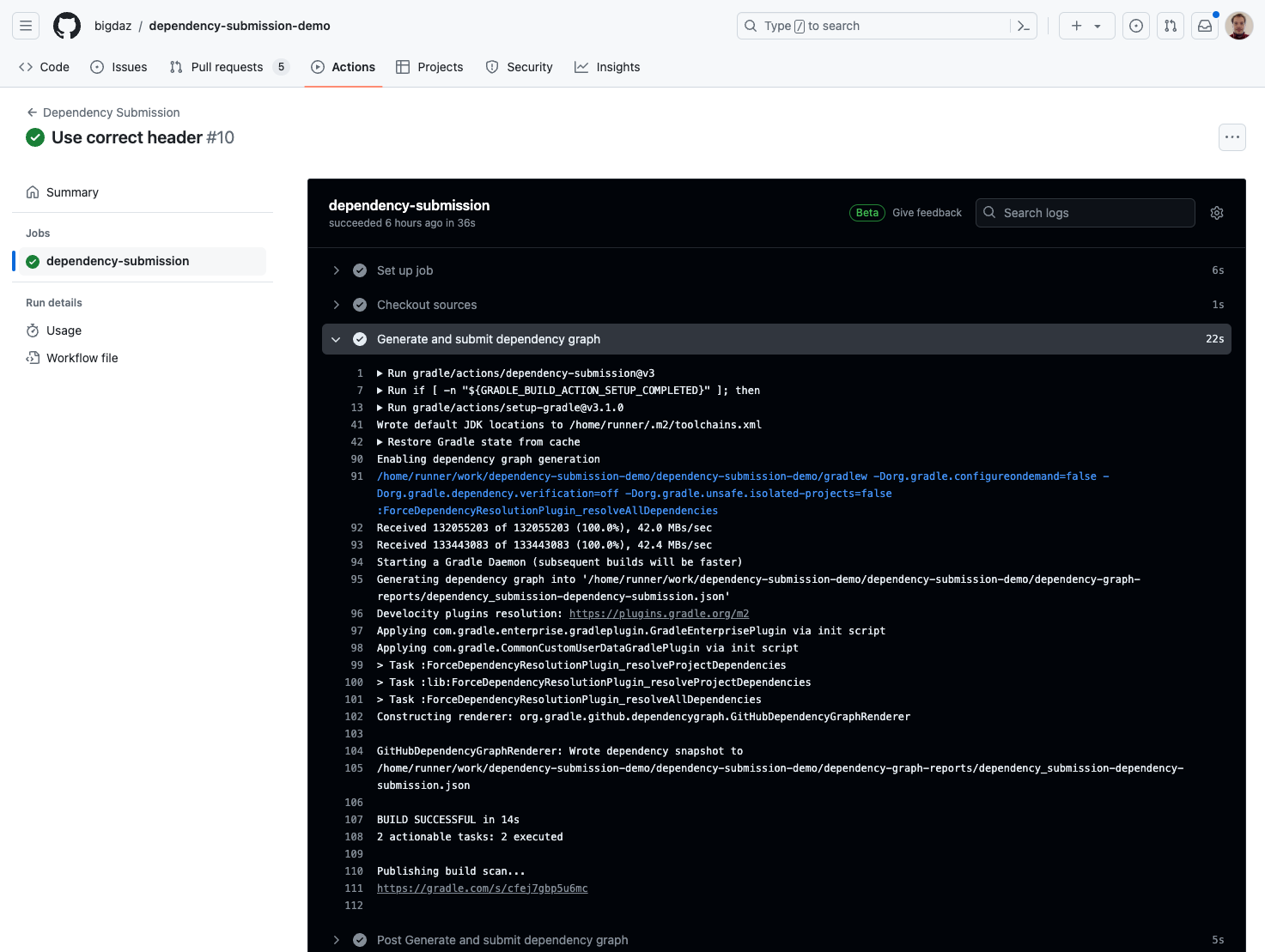
You can find more advanced configurations and settings in the Dependency Submission Action documentation.
How the Dependency Submission Action works #
The key challenge in integrating Gradle Build Tool, GitHub dependency graph, and Dependabot alerts was to provide all dependencies used in the project in their correct versions, considering all of the complexities of the underlying dependency management engine.
In order to provide complete and accurate dependency versions, the Dependency Submission Action for Gradle applies a specialized plugin and runs a small Gradle build that resolves all project dependencies. This means that the submitted dependency versions are exactly the same as those actually used by the project. The action is invoked in a separate workflow step, but will still benefit from optimizations provided by the Setup Gradle Action, and can also use build cache.
Whenever the dependency-submission workflow is run, the GitHub dependency graph is updated with the latest dependency versions for the project. This makes dependency data visible in the Insights > Dependency graph tab of the repository, and enables Dependabot security alerts to be visible with associated notifications sent for any new vulnerabilities.
Get help and share feedback #
We created a dedicated channel for Q&A and discussions.
Join us in our Gradle Community Slack at the #github-integrations channel
for assistance with enabling Dependency Submission Action and fixing vulnerabilities in your project.
We would appreciate any feedback on this channel, too!
If you want to report a defect, please use GitHub Issues on the Gradle actions repository. There, you can also subscribe for new release announcements.
What’s next #
With this GitHub integration, Gradle will help developers deal with vulnerable dependencies, but our goal does not stop there. We plan to continue expanding functionality and adding more features and UX improvements.
To accelerate adoption, Gradle Build Tool engineering team will be submitting pull requests to selected open-source projects that enable the action, starting with Gradle community plugins.
We also want to help maintainers integrate dependency fixes — including those for transitive dependencies — more quickly, and we are contributing to make this easier with Dependabot security updates.
Learn more #
- gradle/actions - Official GitHub Actions for Gradle, including the dependency-submission action.
- gradle/github-dependency-submission-demo - Working example and tutorial on dealing with vulnerable dependencies.
- About supply chain security - Learn more about GitHub Dependency graph, Dependabot alerts and Dependency review.