Verifying Gradle Wrappers with GitHub Actions
We are proud to announce the release of the new Gradle Wrapper Validation GitHub Action.
Gradle Wrapper in Open Source
The gradle-wrapper.jar
is a binary blob of executable code that is checked into nearly
2.8 Million GitHub Repositories.
Searching across GitHub you can find many pull requests (PRs) with helpful titles like ‘Update to Gradle xxx’. Many of these PRs are contributed by individuals outside of the organization maintaining the project.
Maintainers are grateful for these kinds of contributions as it takes an item off of their backlog.
But there are security implications of accepting changes to the Gradle Wrapper binary from external contributors that may not be apparent.
An attacker could take advantage of the trust the open source community has by
hiding malicious code inside the Gradle Wrapper.
A malicious gradle-wrapper.jar could download, install and execute arbitrary code while otherwise behaving like
a completely normal gradle-wrapper.jar.
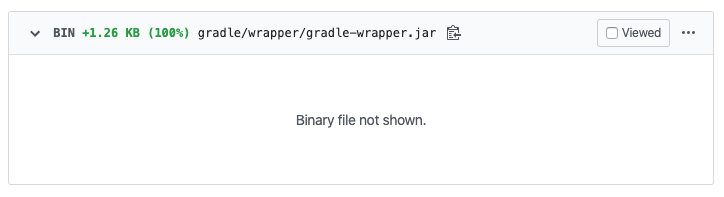
Such an attack could be easily missed as the diff to the gradle-wrapper.jar looks like this.
Verifying the Gradle Wrapper
We have created a
simple GitHub Action
that can be applied to any GitHub repository.
This action will verify that any and all gradle-wrapper.jar files in the repository match an
official SHA-256 checksum.
If any file does not match, the action will fail.
Additionally, the action will detect any homoglyph variants of a file named gradle-wrapper.jar.
The goal is to prevent difficult to spot homoglyph attacks,
like renaming the gradle-wrapper.jar file to gradlе-wrapper.jar (which uses a Cyrillic е instead of e).
Securing Your Project
GitHub actions are free to use for open-source and are automatically enabled by default on almost all repositories. You can find out more about how to add this action to your GitHub repository here.
Existing Users
This action has already been contributed to some of the most popular Gradle based projects on GitHub including but not limited to:
- ReactiveX/RxJava
- ReactiveX/RxAndroid
- junit-team/junit5
- JakeWharton/butterknife
- google/flexbox-layout
- ktorio/ktor
- facebook/fresco
- facebook/flipper
- mockito/mockito
- jhipster/generator-jhipster
- apache/groovy
- apache/lucene-solr
And many more!
Reporting Failures
If this GitHub action fails because a gradle-wrapper.jar doesn’t match one of our published SHA-256 checksums,
we highly recommend that you reach out to us at security@gradle.com.
If you’re curious and want to explore what the differences are between the gradle-wrapper.jar in your possession
and one of our valid releases, you can compare them using this online utility: DiffScope.
Resources
To learn more about verifying the Gradle Wrapper JAR locally (ie. without using GitHub Actions), see our documentation on the topic.